RMF Prepare
CGRC ·NIST Risk Management Framework
RMF Prepare
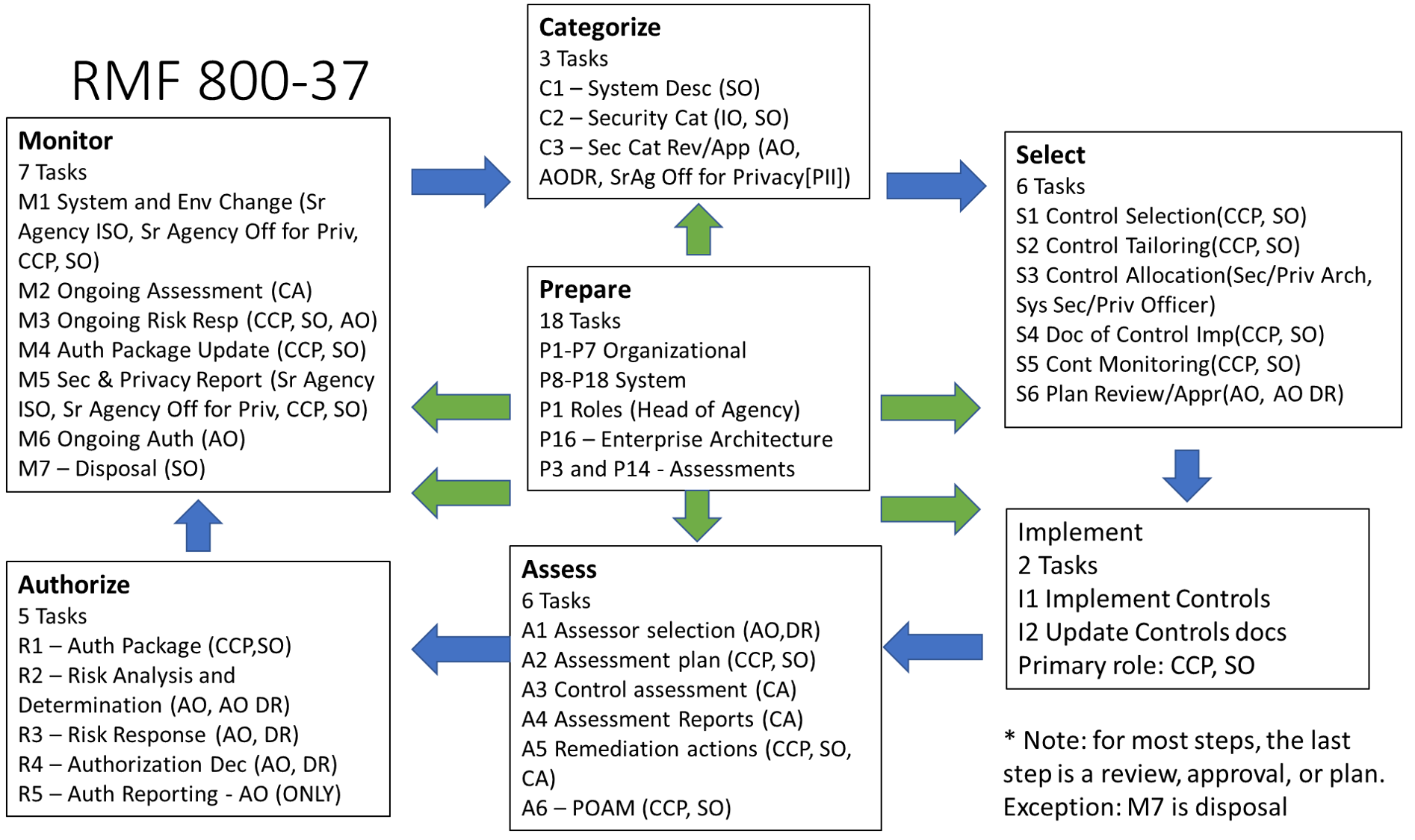
This is the series of articles to use as a study guide for the (ISC)2 CGRC exam. In this article, we will discuss the Prepare steps in the Risk Management Framework.
Organization-level Tasks
- P-1 – Risk Management Roles
- P-2 – Risk Management Strategy
- P-3 – Organization Risk Assessment
- P-4 – Organizationally Tailored Control Baseline and Cybersecurity Profiles (optional)
- P-5 – Common Control identification
- P-6 – Impact level prioritization (optional)
- P-7 – Continuous Monitoring Strategy - organization
Organization-level task details
- P-1 – Risk Management Roles
- Input – organizational security and privacy policies and procedures, organizational charts
- Output – documented Risk Management Framework role assignments
- Primary role – Head of Agency, Chief Information Officer (CIO), Senior Agency for Privacy
- Related tasks – 800-37
- P-2 – Risk Management Strategy
- Input – organizational mission statement, policies, and risk assumptions, constraints, priorities, and trade-offs
- Output – Risk Management strategy and statement of risk tolerance security and privacy risk
- Primary role – Head of Agency
- Related tasks – 800-39 guidance for information security risk program
- P-3 – Organization Risk Assessment
- Input – risk management strategy, mission or business objectives, current threat information, system-level security and privacy risk assessment results, supply chain risk assessment results, previous org-level security and privacy risk assessment results, information-sharing agreements or MOU, security and privacy information for continuous monitoring
- Output – organization-level risk assessment results
- Primary role – Senior Accountable Official for Risk Management, Senior Agency Information Security Officer, Senior Agency Official for Privacy
- Related tasks – 800-30 Reference for conducting a risk assessment
- Reference models – Figure 1.19, 1.20 in book
- Quantitative, Qualitative, and semi- quantitative assessment approaches
- Analysis Approaches: threat-oriented, asset/impact oriented, vulnerability oriented
- P-4 – Organizationally Tailored Control Baseline and Cybersecurity Profiles (optional)
- Input – documented security and privacy requirements directing the use of organizationally tailored control, business objectives, enterprise/security/privacy architectures, risk assessment results (org and sys), list of common control providers, 800-53B control baselines
- Output – list of approved or directed organizationally tailored control baselines, cybersecurity framework profiles
- Primary role – Senior Accountable Official for Risk Management, Mission or Business Owner
- P-5 – Common Control identification
- Input – documented security and privacy requirements, existing common control providers and associated security and privacy plans, information security and privacy program plans, org and system level security and privacy risk assessment results
- Output – list of common control providers and common controls available for inheritance, security and privacy plans providing a description of common control implementation
- Primary role – Senior Agency for Information Security Officer, Senior Agency Official for Privacy
- P-6 – Impact level prioritization (optional)
- Input – security categorization information for organizational systems, system descriptions, org and system level risk assessment results, business objectives, cybersecurity framework profiles
- Output – organizational systems prioritized into low, moderate, high impact categories
- Primary role – Senior Accountable Official for Risk Management
- P-7 – Continuous Monitoring Strategy - organization
- Input – risk management strategy, org and system level risk assessment results, org security and privacy policies
- Output – implemented organizational continuous monitoring strategy
- Primary role – Senior Accountable Official for Risk Management
System-level Tasks
- P-8 – Mission and business focus
- P-9 – System stakeholders
- P-10 – Asset identification
- P-11 – Authorization boundary
- P-12 – Information types
- P-13 – Information life cycle
- P-14 – System Risk Assessment
- P-15 – Requirements definition
- P-16 – Enterprise Architecture
- P-17 – Requirements allocation
- P-18 – System registration
System-level task details
- P-8 – Mission and business focus
- Input – org mission statement and policies, mission/business process information, system stakeholder information, cybersecurity framework policies, request for proposals or acquisition documents, concept of operations
- Output – mission, business functions and mission/business processes that the system will support
- Primary role – Mission or Business Owner
- P-9 – System stakeholders
- Input – organizational mission statement, mission/business objectives; mission, business functions, and processes hat the system will support, org security and privacy policies and procedures, org charts, information about individuals or groups that have an interest or decision-making responsibility
- Output – list of system stakeholders
- Primary role – Mission or Business Owner, System Owner
-
Secondary roles - Sr Agency ISO, Sr Agency Off for Priv, CCP, SO
- SDLC – initiation
- P-10 – Asset identification
- Input – mission/business functions and processes the information system will support, BIA, internal stakeholders, system stakeholder information, system information, information about systems that will interact with the system
- Output – set of assets to be protected
- Primary role – System Owner
- SDLC – initiation
- Tangible (facilities, humans, equipment, networks), Intangible (processes, functions, data, firmware, software, services)
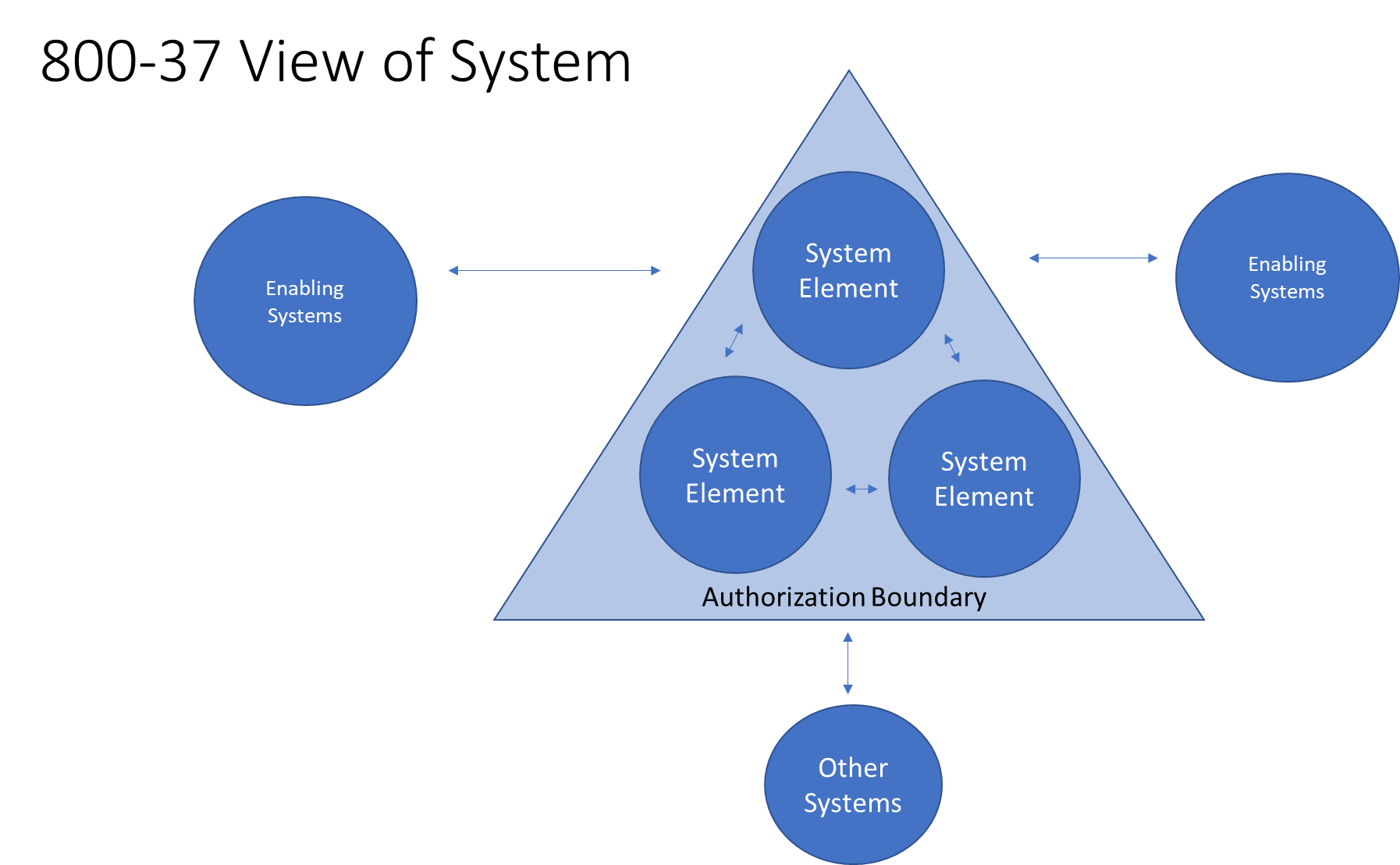
- P-11 – Authorization boundary
- Input – system design documentation, network diagrams, system stakeholder information, asset information, network/enterprise architecture diagrams, org structure
- Output – documented authorization boundary
- Primary role – Authorizing Official
- SDLC – initiation
- P-12 – Information types
- Input – system design documentation, assets to be protected, mission/business process information
- Output – list of information types for the system
- Primary role – Information Owner or Steward, System Owner (SO)
- SDLC – initiation
- P-13 – Information life cycle
- Input – missions, business functions, and mission/business processes the system will support; system stakeholder information, authorization boundary information, information about systems that will interact, system design documentation, system element information, list of system information types
- Output – documentation of the stages of information passing in the system.
- Primary role – Senior Agency Official for Privacy, IO, SO
- SDLC – initiation
- Create, Process, Dissemination (Share), Use, Storage, Disposition
- P-14 – System Risk Assessment
- Input – assets to be protected; missions, business functions, and mission/business processes the system will support; business impact analysis (BIA) or criticality analysis; system stakeholder information; provider information; threat information; data map; system design documentation; cybersecurity framework profiles; risk management strategy; organization-level risk assessment results
- Output – Security and privacy risk assessment reports
- Primary role – SO, System Security/Privacy Officer
- Related tasks – 800-30 Reference for conducting a risk assessment
- SDLC – initiation
- P-15 – Requirements definition
- Input – system design documentation, org and system level risk assessment results, set of stakeholder assets to be protected, functions and processes the system will support, BIA, system stakeholder information, data map of information life cycle for PII, cybersecurity framework policies, information about systems that will interact, supply chain information, threat information; laws, exec orders, directives, regulations, and policies that apply to the system, risk management strategy
- Output – Documented security and privacy requirements
- Primary role – SO, System Privacy Officer
- SDLC – initiation
- P-16 – Enterprise Architecture
- Input – security and privacy requirements, org and system level risk assessment results, enterprise architecture information, security architecture information, privacy architecture information, asset information
- Output – update enterprise architecture, security architecture, privacy architecture; plans to use cloud-based systems, shared systems, services, or applications
- Primary role – Enterprise Architect, Mission or Business Owner, Security/Privacy Architect
- SDLC – initiation
- P-17 – Requirements allocation
- Input – org and system level risk assessment results, documented security and privacy requirements, list of common control providers, system description, system element information, system component inventory, relevant laws, exec orders, directives, regulations, and policies
- Output – list of security and privacy requirements allocated to the system, system elements, and environment of operation
- Primary role – Security/Privacy Architect, System Security/Privacy Officer
- SDLC – initiation
- P-18 – System registration
- Input – organizational policy on system registration, system information
- Output – registered system in accordance with organizational policy
- Primary role – System Owner (SO)
- SDLC – initiation
- The registration of a system informs the governing organization of plans to develop a system and facilitates system tracking and integration with enterprise architectures
The prepare tasks input to other tasks throughout the Risk Management Framework process. Unlike the remaining steps and tasks, prepare does not interact with the other steps in a linear manner.
