RMF Assess
CGRC ·NIST Risk Management Framework
RMF Assess
This is the series of articles to use as a study guide for the (ISC)2 CGRC exam. In this article, we will discuss the Assess steps in the Risk Management Framework.
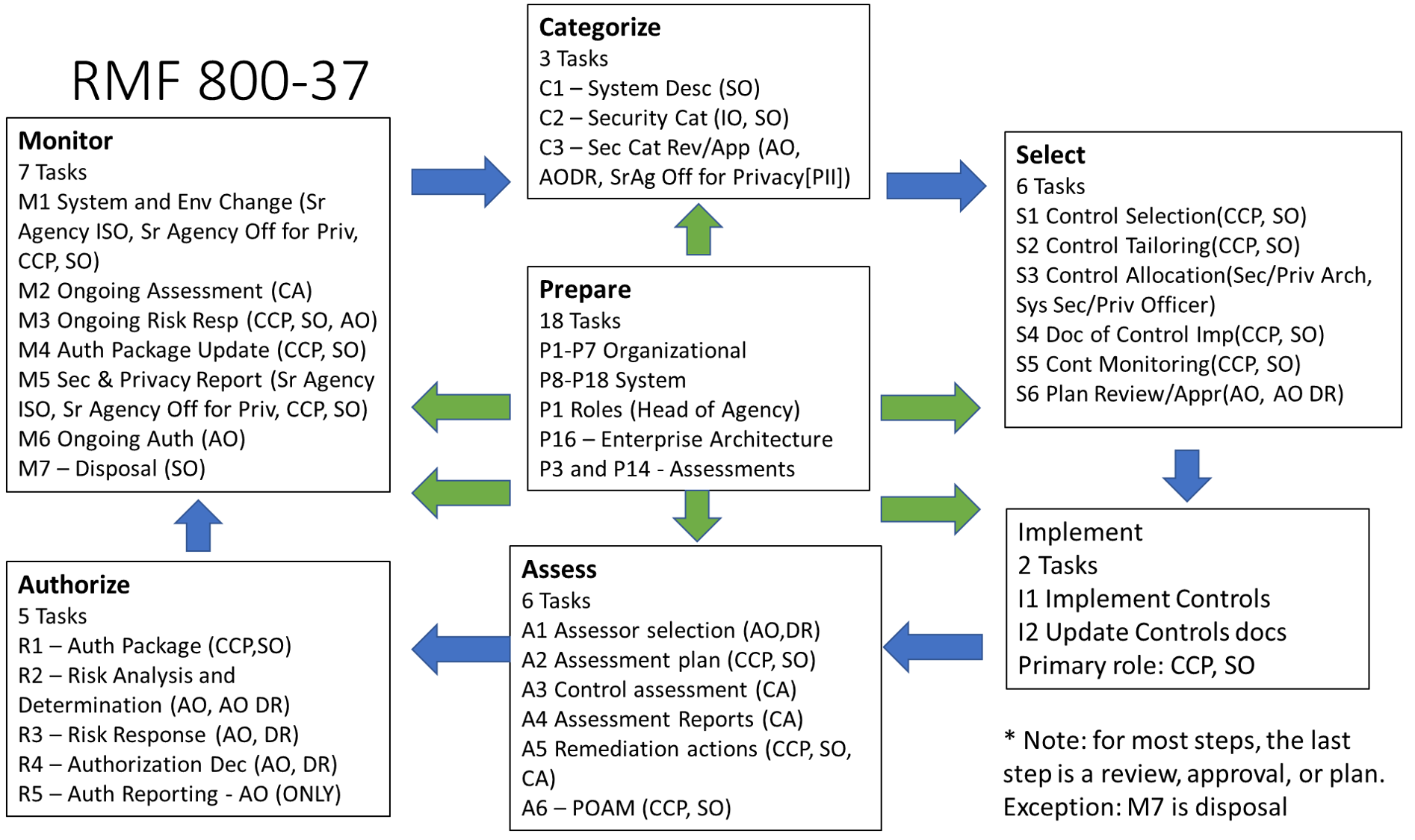
Assess Tasks
- A-1 – Assessor selection
- A-2 – Assessment plan
- A-3 – Control assessment
- A-4 – Assessment Reports
- A-5 – Remediation actions
-
A-6 – Plan of Action and Milestones
- 800-30
- 800-55 Performance measurement guide for information security
- Implementation, effectiveness/efficiency, and impact
- Considerations: organizational, manageability, data management, automation
- 800-115 guidance and technical implementation for testing and assessment techniques
Assess Task Details
- A-1 – Assessor selection
- Input – security and privacy and SCRM plans, policies and procedures, program management control information, common control documentation, org security and privacy program plans, SCRM strategy, system design documentation, enterprise, security and privacy architecture
- Output – selection of assessor or assessment team for control assessment
- Primary role – AO or AO DR
- Related tasks – I-2, P-16
- SDLC – development/acquisition
- A-2 – Assessment plan
- Input – security and privacy and SCRM plans, policies and procedures, program management control information, common control documentation, org security and privacy program plans, SCRM strategy, system design documentation, enterprise, security and privacy architecture
- Output – security and privacy assessment plans approved by the authorizing official
- Primary role – AO AODR CA
- Related tasks – I-2. P-16
- SDLC – development/acquisition
- Object – AIMS
- Methods – TIE
- Security Control Classes – MOT
- Methods
- Test, Interview, Examine
- 800-53A – Assessment Procedure (AU-7)
- 800-161 – Supply chain risk management
- A-3 – Control assessment
- Input – security and privacy assessment plans, security and privacy plans, external assessment or audit results
- Output – completed control assessment and associated assessment evidence
- Primary role – Control Assessor (CA)
- Related tasks – I2, A2, P5, P16
- SDLC – development/acquisition
- NIST Interagency report 8011 – automated assessment can replace manual control assessment when automated is at least as timely, and at least as compliant.
- 800-160 two concepts (processes) – verification (did you build it right?) and validation (did you build the right thing?)
- A-4 – Assessment Reports
- Input – completed control assessments and associated assessment evidence
- Output – completed security and privacy assessment reports detailing the assessor findings and recommendations
- Primary role – Control Assessor (CA)
- Related tasks – A3,
- SDLC – development/acquisition
- A-5 – Remediation actions
- Input – completed assessment reports, security and privacy plans and assessment plans, org-level and system-level risk assessment results
- Output – completed initial remediation actions based on the assessment reports, changes to implementation reassessed, updated security and privacy assessment reports, and update plans including control implementation changes
- Primary role – CCP and SO and CA
- Related tasks – I2, A4, P3, P14
- SDLC – development/acquisition
- Risk response – avoidance, mitigation, transfer, acceptance.
- A-6 – Plan of Action and Milestones
- Input – updated security and privacy assessment reports and plans, org and system-level risk assessment results, org risk management strategy and risk tolerance
- Output – plan of action and milestones detailing the findings from the security and privacy assessment reports
- Primary role – CCP and SO
- Related tasks – I2, A4, A5, P2, P3, P14
-
SDLC – development/acquisition
- A-6 – Plan of Action and Milestones
- MUST include
- Weakness identified
- Point of contact
- Resources required to correct
- Scheduled completion date for correction
- Milestones with completion dates
- Changes to milestones
- Method of identification
- Status
After the assessment has been completed, you will be ready to move to authorize the security and privacy plan, and risk assessment package.
