RMF Monitor
CGRC ·NIST Risk Management Framework
RMF Monitor
This is the series of articles to use as a study guide for the (ISC)2 CGRC exam. In this article, we will discuss the Monitor steps in the Risk Management Framework.
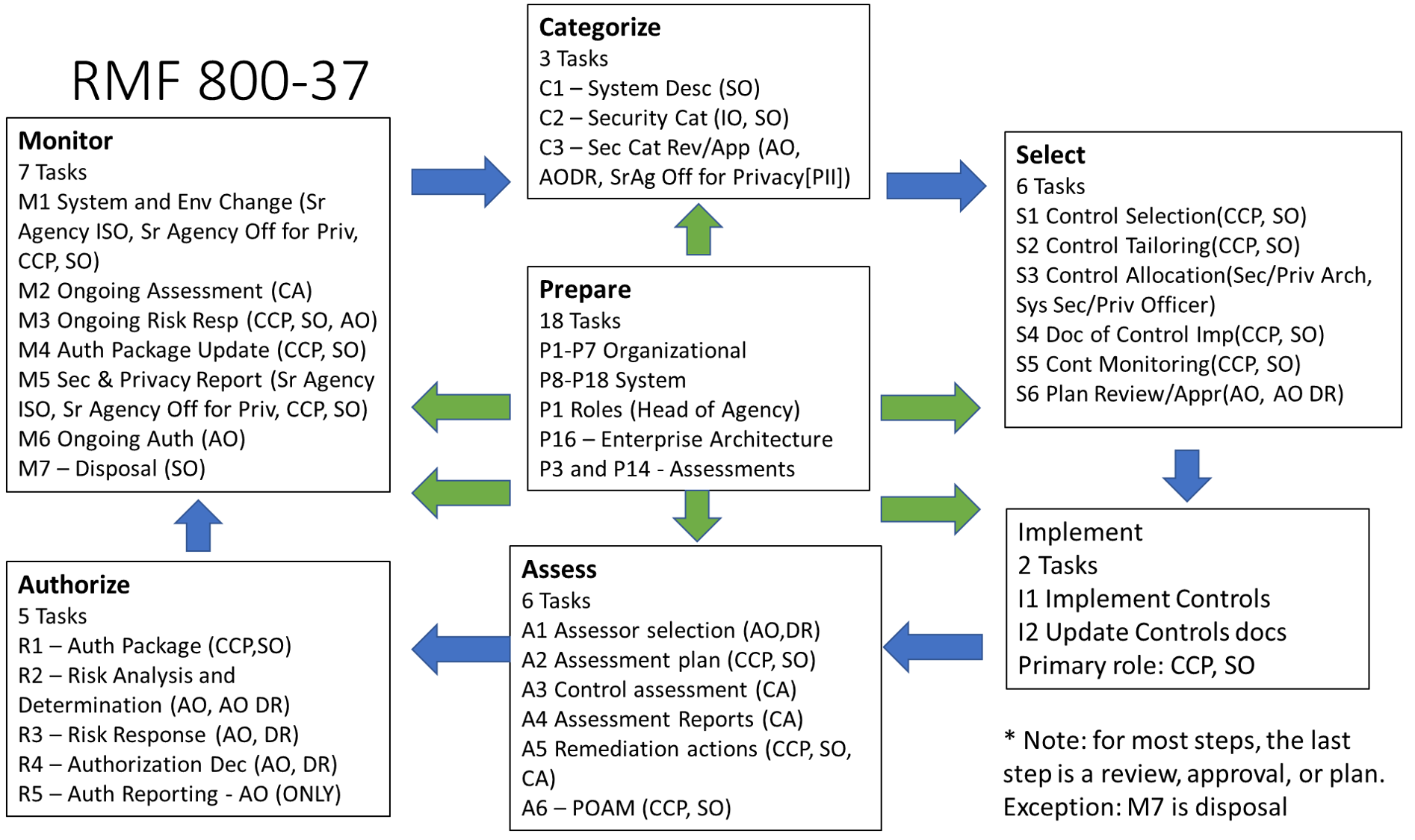
Monitor Tasks
- M-1 – System and Environment changes
- M-2 – Ongoing Assessments
- M-3 – Ongoing Risk Response
- M-4 – Authorization Package Updates
- M-5 – Security and Privacy Reporting
- M-6 – Ongoing Authorization
-
M-7 – System Disposal
- 800-137 Information Security Continuous Monitoring – don’t eat iguanas at Red Robin.
Monitor Task Details
- M-1 – System and Environment changes
- Input – organizational and system strategies, policies, and procedures, system design documentation, continuous monitoring strategy
- Output – updated security and privacy plans, plans of action and milestones, security and privacy assessment reports
- Primary role – Senior Agency Information Security Officer, Senior Agency Official for Privacy, CCP and SO
- Related tasks – P7, R1
- SDLC – operations/maintenance for new and existing
- Configuration management concepts:
- policy and procedures (CM-1),
- management plan (CM-9),
- control board,
- component inventory (CM-8),
- configuration items,
- change control (CM-3),
- Security Impact Analysis (CM-4),
- baseline configuration (CM-2),
- configuration monitoring.
- M-2 – Ongoing Assessments
- Input – org continuous monitoring strategy, security and privacy plans and assessment plans and reports, plan of action and milestones, information from automated and manual monitoring tools, org and system level assessment results, external assessment or audit results
- Output – updated security and privacy assessment reports
- Primary role – Control Assessor
- Related tasks – P2, P3, P14, P7, R1, R4
- SDLC – operation/maintenance
- Ongoing assessments include:
- Formal assessments,
- informal assessments,
- configuration scanning,
- vulnerability scanning,
- review of logs and event data
- M-3 – Ongoing Risk Response
- Input – security and privacy assessment reports, org and system level risk assessment reports, security and privacy plans, plans of action and milestones
- Output – mitigation actions or risk acceptance decisions, updated security and privacy assessment reports
- Primary role – CCP and SO and AO
- Related tasks – P3, P14, R1, M1
- SDLC – operations/maintenance
- Cyber threat response
- M-4 – Authorization Package Updates
- Input – security and privacy assessment reports and plans, org and system level risk assessment results, POAM
- Output – updated inputs
- Primary role – CCP and SO
- Related tasks – P3, P14, R1
- SDLC – operations/maintenance
- M-5 – Security and Privacy Reporting
- Input – security and privacy assessment reports and plans, org and system level risk assessment results, POAM, cybersecurity framework profile
- Output – Security and Privacy posture reports
- Primary role – CCP and SO, Senior Agency Information Security Officer, Senior Agency Official for Privacy
- Related tasks – P3, P14, P7, R1
- SDLC – operations/maintenance
- M-6 – Ongoing Authorization
- Input – risk tolerance, security and privacy posture reports, POAM, org and system level risk assessment results, security and privacy plans
- Output – determination of risk, ongoing authorization to operate, use, and common control authorization (or denial of each)
- Primary role – AO
- Related tasks – P2, P3, P14, R1, R4, M5
- SDLC – operations/maintenance
- M-7 – System Disposal
- Input – security and privacy plans, org and system level risk assessment results, system component inventory
- Output – disposal strategy, updated system component inventory, updated security and privacy plans
- Primary role – SO
- Related tasks – P3, P14, R1
- SDLC – New: not applicable, existing: Disposal
- Sanitize – clear, purge, destroy
- Crytographic erasure
Continuous monitoring within your risk management framework creates a methodology for continuous authorization and assessment of security and privacy controls for the system.
