Posts
My thoughts and ideas
My thoughts and ideas
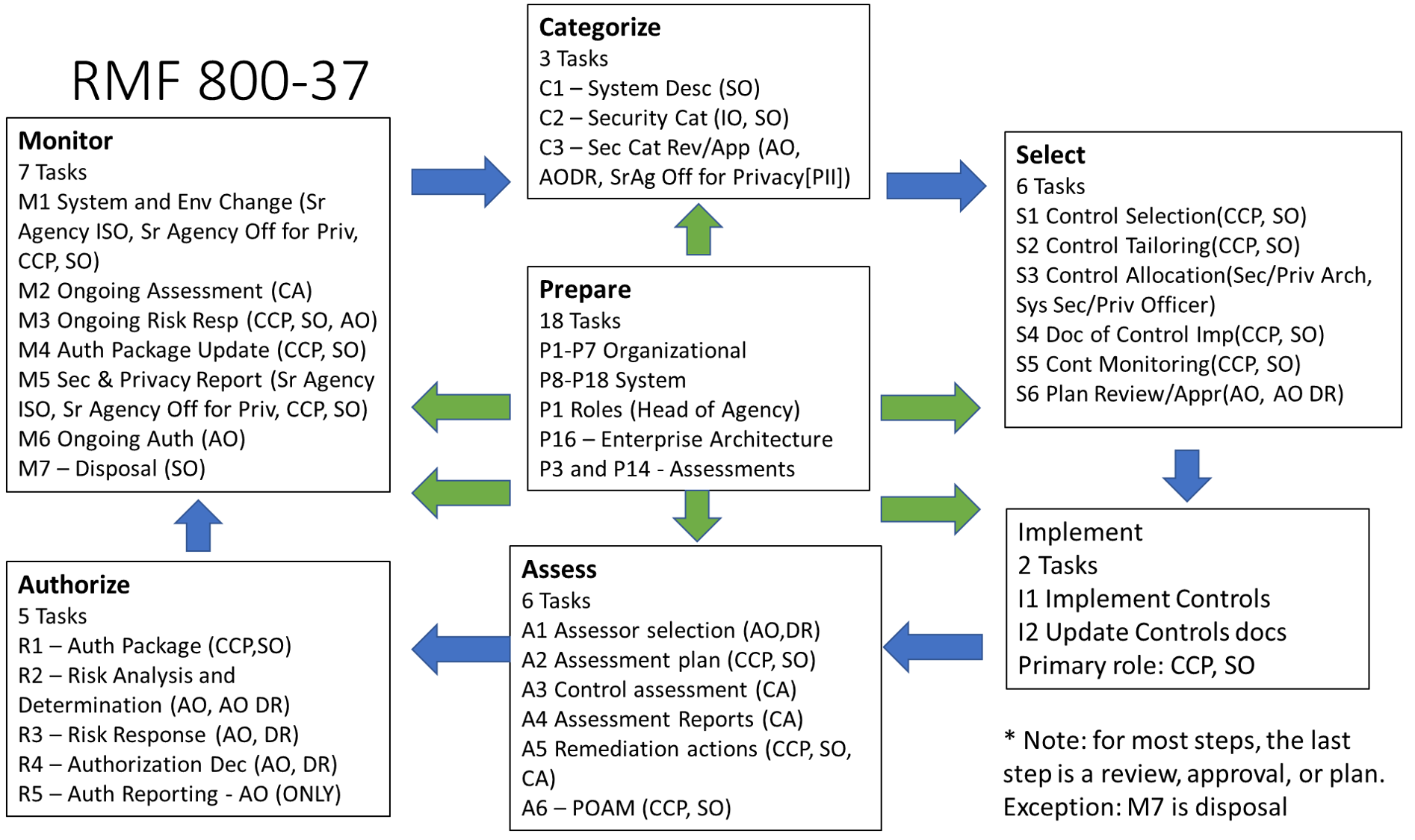
This is the series of articles to use as a study guide for the (ISC)2 CGRC exam. In this article, we will discuss the Select steps in the Risk Management Framework.

This is the series of articles to use as a study guide for the (ISC)2 CGRC exam. In this article, we will discuss the Categorize steps in the Risk Management Framework.
FIPS 199
CMSS 1253

This is the series of articles to use as a study guide for the (ISC)2 CGRC exam. In this article, we will discuss the Prepare steps in the Risk Management Framework.

This is the first of a series of articles to use as a study guide for the (ISC)2 CGRC exam.

More information can be found at the Azure Back to School site: https://azurebacktoschool.github.io
Azure Back to School is back again this year. Last year, we had enough participants to have 1-2 presentations daily for all 30 days of September. I’d like to have twice this many...